This forensic appendix outlines forensic evidence on the use of highly invasive spyware against two journalists from India. Our investigation confirms that the devices of both individuals were targeted with NSO Group’s Pegasus spyware between August and October 2023. More information about the context for these attacks is available in an accompanying press release.
This is not the first time Amnesty International found evidence of unlawful targeted surveillance against civil society in India. In 2020, Amnesty International and Citizen Lab revealed how human rights defenders were targeted in a coordinated surveillance operation using commercial off-the-shelf spyware. As part of the Pegasus Project, Amnesty International revealed how numerous civil society members and journalists in India and around the world were targeted and infected using NSO Group’s Pegasus spyware.
In June 2023, as part of our regular technical monitoring efforts, the Amnesty Security Lab observed network indicators suggesting that a Pegasus customer was again active with an interest in targeting individuals in India. Subsequent forensic findings, published here, confirm that the NSO Group’s Pegasus spyware is once again a threat to civil society and journalists in India.
Amnesty International is grateful for the assistance of the Reporters Without Borders Digital Security Lab in this investigation.
Anand Mangnale
Anand Mangnale is an investigative journalist and South Asia Editor at The Organised Crime and Corruption Report Project (OCCRP). He received a threat notification from Apple in October 2023. Following the alert, he shared forensic records from his phone with Amnesty International for analysis.
An analysis of Anand Mangnale’s phone uncovered forensic evidence consistent with targeting using NSO Group’s zero-click BLASTPAST exploit on 23 August 2023. At the time, his iPhone 13 Pro was running iOS version 16.6 which was the iOS release available at the time of the attack.
The NSO Group BLASTPAST exploit was publicly identified and disclosed by Citizen Lab in September 2023, and patched by Apple in iOS 16.6.1 (CVE-2023-41064 and CVE-2023-41061) on 7 September 2023.
Similar to other recent Pegasus zero-click attacks, this exploit involves two distinct phases. An initial stage interacts with the Apple HomeKit service, and a second stage where malicious attachment files are sent to the target device over the iMessage service. The two-stage attack process seen in this case is similar to the previous PWNYOURHOME Pegasus attack vector described by Citizen Lab and independently observed by the Security Lab.
The Security Lab recovered multiple samples of NSO Group’s BLASTPAST exploit sent to Anand Mangnale’s iPhone on 23 August 2023 in an attempt to install Pegasus on his device. These .pkpass exploit payloads were delivered to his device following a large number numerous HomeKit crashes on his device. These forensic traces are described in greater detail in the later BLASTPAST section which details the forensic traces observed in this attack. It is unclear if this attack succeeded in installing the Pegasus spyware agent on his phone.
| Timestamp (UTC) | Trace |
| 2023-08-23 10:13:44 | Library/SMS/Attachments/a8/08/EB8689DD-D978-4F96-B372-E2F1B47703F4/sample.pkpass |
| 2023-08-23 10:14:50 | Library/SMS/Attachments/d2/02/51F1F524-9053-40B2-A42F-04032505C1F9/sample.pkpass |
| 2023-08-23 10:15:59 | Library/SMS/Attachments/c8/08/B8FF4B47-F81F-43EE-88D4-F01239F4DBB4/sample.pkpass |
| 2023-08-23 10:17:42 | Library/SMS/Attachments/63/03/4EDB5554-CACF-4979-A00B-C24D39F898A3/sample.pkpass |
| 2023-08-23 10:18:49 | Library/SMS/Attachments/ed/13/FB2CAA27-10E7-449A-AC13-155494DB9BD5/sample.pkpass |
| 2023-08-23 10:19:56 | Library/SMS/Attachments/a9/09/3D0C29E4-5535-4D77-ADD9-29F83AE1197E/sample.pkpass |
| 2023-08-23 10:21:39 | Library/SMS/Attachments/10/00/E921653A-A707-428B-9B4B-50D6F3FD56E6/sample.pkpass |
| 2023-08-23 10:22:47 | Library/SMS/Attachments/66/06/BA9BB593-1177-409D-A761-954FF187E81A/sample.pkpass |
Through an analysis of HomeKit related logs, the Security Lab was able to identify an attacker email address, [email protected] which was used to deliver the initial stage of the Pegasus infection attempt over HomeKit. This iCloud account was the only email account referenced in the reviewed HomeKit logs on the device, excluding the iCloud account used by Anand Mangnale himself.
Siddharth Varadarajan
Siddharth Varadarajan is an Indian investigative journalist and Founding Editor of The Wire. Amnesty International has previously identified forensic evidence that his devices were targeted and successfully compromised with NSO Group Pegasus spyware in April 2018.
In October 2023, Siddharth Varadarajan also received a threat notification from Apple informing him that his phone may be targeted by “state-sponsored attackers”. The Security Lab reviewed forensic records from Siddharth Varadarajan’s iPhone 11 and identified traces which confirms that his phone was also target with NSO Group’s Pegasus spyware in October 2023.
HomeKit logs from Siddharth Varadarajan iPhone show that the was also targeted by the same Pegasus attacker email account used to target Anand Mangnale. The recovered HomeKit logs show that the [email protected] Apple account interacted with his device’s HomeKit service on 16 October 2023 around 14:36:09 UTC. At the time his phone was running iOS version 16.6.1 which was not vulnerable to the BLASTPAST attack.
| Timestamp (UTC) | Trace |
| 2023-10-16 14:36:09 | Interaction with HomeKit service from iCloud account [email protected] (#1) |
| 2023-10-16 14:36:09 | Interaction with HomeKit service from iCloud account [email protected] (#2) |
There is no evidence to suggest that Siddharth Varadarajan device was successfully compromised on this occasion. The initial HomeKit request may be involved in fingerprinting the device or preparing the device for further exploitation. A remote attacker may need to interact with other device applications to identify if a device is vulnerable to a particular exploit before sending the full zero-click payload.
Forensic traces of NSO Group BLASTPASS exploit
The following forensic records and traces were recovered from the Anand Mangnale iPhone 13 Pro.
Around 23 August 2023 09:51:00 UTC, numerous crashes began to occur in the `homed` process of the Apple HomeKit service on his device. These crashes resulted in almost two dozen `homed` crash reports being reports being generated on the device.
| Crash Timestamp (UTC) | Crash Type |
| 2023-08-23 09:51:21 | Crash of process homed for reason EXC_CRASH (SIGABRT) |
| 2023-08-23 09:51:32 | Crash of process homed for reason EXC_CRASH (SIGABRT) |
| 2023-08-23 09:51:33 | Crash of process homed for reason EXC_CRASH (SIGABRT) |
| 2023-08-23 09:51:45 | Crash of process homed for reason EXC_CRASH (SIGABRT) |
| 2023-08-23 09:51:54 | Crash of process homed for reason EXC_CRASH (SIGABRT) |
| 2023-08-23 09:52:05 | Crash of process homed for reason EXC_CRASH (SIGABRT) |
| 2023-08-23 09:52:15 | Crash of process homed for reason EXC_CRASH (SIGABRT) |
| 2023-08-23 09:53:07 | Crash of process homed for reason EXC_CRASH (SIGABRT) |
| 2023-08-23 09:53:18 | Crash of process homed for reason EXC_CRASH (SIGABRT) |
| 2023-08-23 09:53:28 | Crash of process homed for reason EXC_CRASH (SIGABRT) |
| 2023-08-23 09:53:39 | Crash of process homed for reason EXC_CRASH (SIGABRT) |
| 2023-08-23 09:53:50 | Crash of process homed for reason EXC_CRASH (SIGABRT) |
| 2023-08-23 09:54:00 | Crash of process homed for reason EXC_CRASH (SIGABRT) |
| 2023-08-23 09:54:10 | Crash of process homed for reason EXC_CRASH (SIGABRT) |
| 2023-08-23 09:54:21 | Crash of process homed for reason EXC_CRASH (SIGABRT) |
| 2023-08-23 09:54:31 | Crash of process homed for reason EXC_CRASH (SIGABRT) |
| 2023-08-23 09:54:42 | Crash of process homed for reason EXC_CRASH (SIGABRT) |
| 2023-08-23 09:54:53 | Crash of process homed for reason EXC_CRASH (SIGABRT) |
| 2023-08-23 09:55:04 | Crash of process homed for reason EXC_CRASH (SIGABRT) |
| 2023-08-23 09:55:14 | Crash of process homed for reason EXC_CRASH (SIGABRT) |
| 2023-08-23 09:55:24 | Crash of process homed for reason EXC_CRASH (SIGABRT) |
| 2023-08-23 09:55:37 | Crash of process homed for reason EXC_CRASH (SIGABRT) |
| 2023-08-23 10:05:21 | Crash of process homed for reason EXC_CRASH (SIGABRT) |
The crash report files show the crashes occurring while homed was apparently processing objects received remotely over the Apple Push Notification service with NSKeyedUnarchiver.
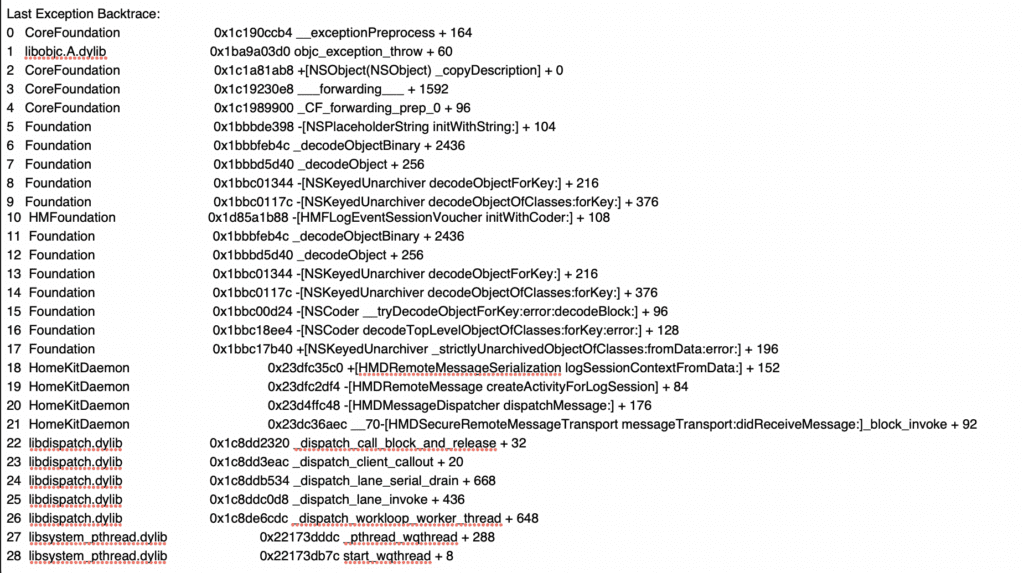
Soon after the series of ‘homed’ process crashes, his device was sent multiple malicious .pkpass files as attachments over iMessage. Each attachment file was named “sample.pkpass”. These PKPASS files contained an embedded webp image which would be automatically loaded and parsed on the device without user interaction. The embedded webp image is a zero-click exploit which attempt to gain remote code execution by exploiting a vulnerability in the libwebp library bundled in the Apple ImageIO framework (CVE-2023-4863). The webp vulnerability was a zero-day unpatched flaw at the time the attachment was sent.
| 2023-08-23 10:13:44 | Library/SMS/Attachments/a8/08/EB8689DD-D978-4F96-B372-E2F1B47703F4/sample.pkpass |
| 2023-08-23 10:14:50 | Library/SMS/Attachments/d2/02/51F1F524-9053-40B2-A42F-04032505C1F9/sample.pkpass |
| 2023-08-23 10:15:59 | Library/SMS/Attachments/c8/08/B8FF4B47-F81F-43EE-88D4-F01239F4DBB4/sample.pkpass |
| 2023-08-23 10:17:42 | Library/SMS/Attachments/63/03/4EDB5554-CACF-4979-A00B-C24D39F898A3/sample.pkpass |
| 2023-08-23 10:18:49 | Library/SMS/Attachments/ed/13/FB2CAA27-10E7-449A-AC13-155494DB9BD5/sample.pkpass |
| 2023-08-23 10:19:56 | Library/SMS/Attachments/a9/09/3D0C29E4-5535-4D77-ADD9-29F83AE1197E/sample.pkpass |
| 2023-08-23 10:21:39 | Library/SMS/Attachments/10/00/E921653A-A707-428B-9B4B-50D6F3FD56E6/sample.pkpass |
| 2023-08-23 10:22:47 | Library/SMS/Attachments/66/06/BA9BB593-1177-409D-A761-954FF187E81A/sample.pkpass |
The .pkpass attachments were automatically loaded and parsed inside the BlastDoor sandbox. This resulted in numerous crashes in the MessagesBlastDoorService service as each pkpass file was parsed and attempted to gain code execution and escape from the sandbox. It appears the exploit successfully achieved initial code execution.
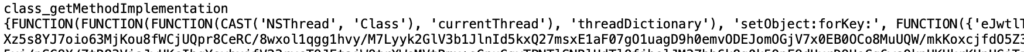
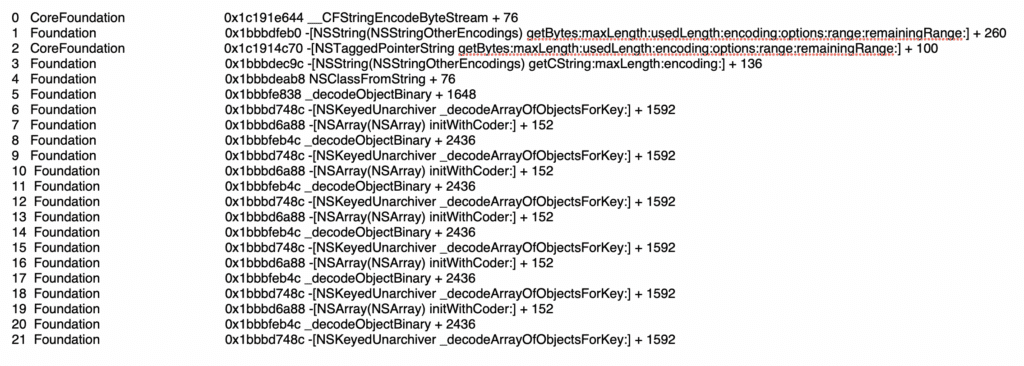
One sample crash report from the MessagesBlastDoorService shows a EXC_BAD_ACCESS (KERN_PROTECTION_FAILURE) exception. The accompanying stack trace shows a long sequence of calls to the NSKeyedUnarchiver function `_decodeArrayOfObjectsForKey`. Such NSExpression primitives have been used in multiple recent in-the-wild exploit chains including NSO Group’s 2021 FORCEDENTRY exploit and a 2023 exploit analysed by Google Project Zero.
The webp image itself contains plaintext NSExpressions which appear to decode embedded Base64 encoded blobs containing encrypted subsequent stages of the exploit. It was not possible to decrypt or recover the later stages of the attack.